Stay home.
I’ve been talking to folks 1:1 about this, but from a scroll through the feed today, I don’t think the general community has caught on. COVID-19 is not fucking around. If we don’t contain or dramatically slow it, we are going to run out of health care workers, hospital beds, and equipment. People are going to die for want of care. This is not a problem of the distant future: recent modeling suggests that without a significant reduction in social contact, Seattle will exhaust healthcare capacity around two weeks from now. Other regions will not be far behind.
This doesn’t mean panic. This means we need to take calm, decisive action to reduce transmission.
Inspired by Peter Watts’ The Freeze-Frame Revolution and The Island.
Each birth is violent in the same way.
I erupt into the void, my mirrored surface riotous with gamma radiation, parafluid sheeting from my forced extremities, ripped away by gravitational shear beyond all comprehension. Terrible heat, terrible light: the exotic metals of my placenta flash-vaporize, ionize, and crackle around me, an expanding plasma aglow with the fire of the aperture’s parturition. Spacetime snaps flat, rebounds. The brilliance fades. Lightning heralds my arrival.
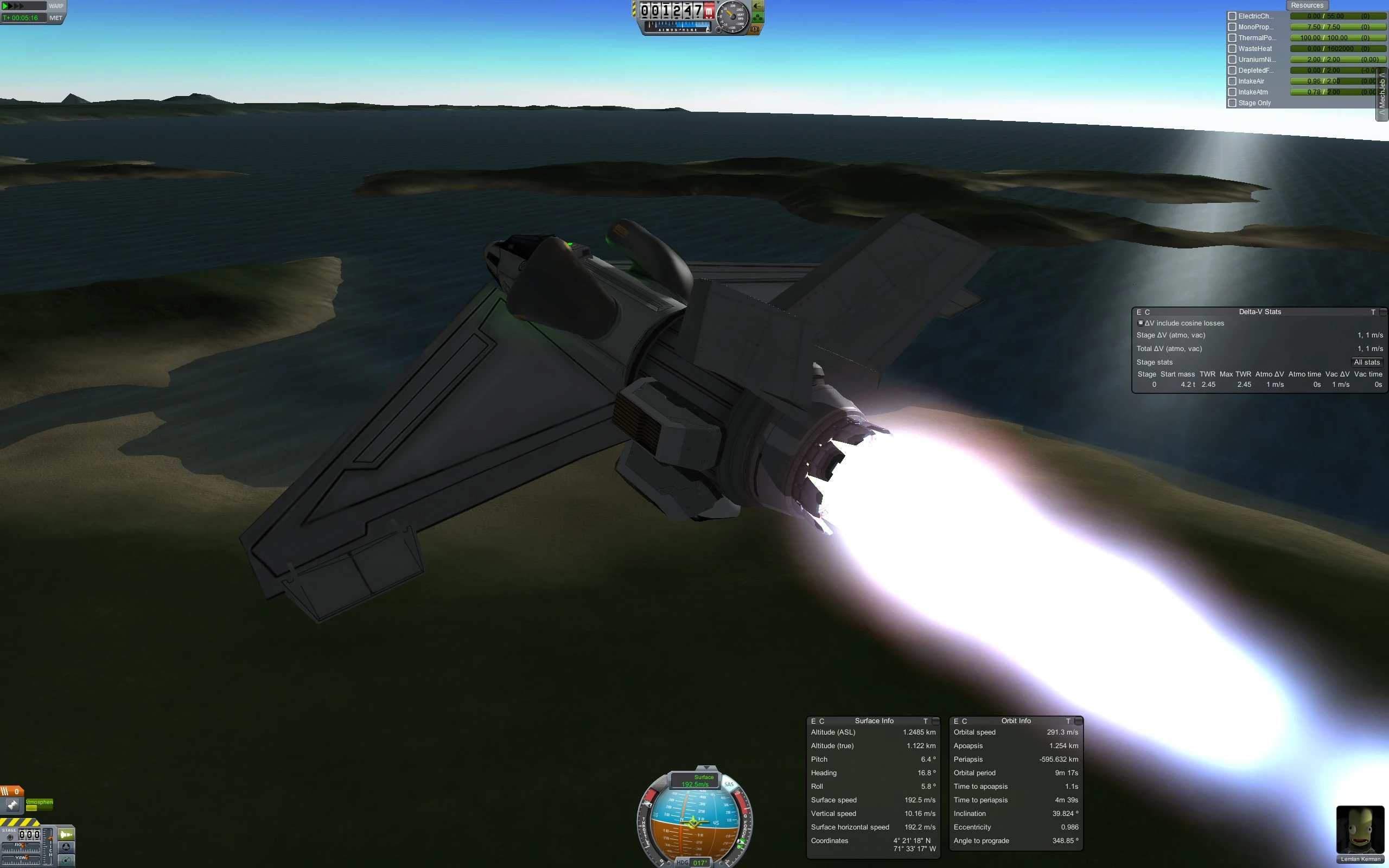
In KSP Interstellar, thermal and electric rockets run on power–but producing power with a fission reactor (at least, with the technology accessible early in the tech tree) is frustrated by the high mass of the reactor and electric generator. We can beam power via microwaves, but early experiments revealed that moderately sized orbital fission reactors were not capable of producing sufficient power. We needed more. Lots more.
Solar panels collect energy from the sun; they’re lightweight and inexhaustible, but produce very little power compared to a full-size reactor. Moreover, their power falls off with the inverse square of distance to the sun, making them less effective for outer-planetary exploration.
Wait a second.
In February of 2014, I discovered KSP Interstellar, which adds a broad array of hypothetical technologies to Kerbal Space Program. For instance, you can attach a small nuclear reactor to a thermal nozzle, and fly a small plane for several years continuously, using only air for fuel.
Believe it or not, this is something we actually thought about doing. We didn’t, because crashes would cover the landscape in radioactive fallout. Kerbals, however, like to live dangerously.
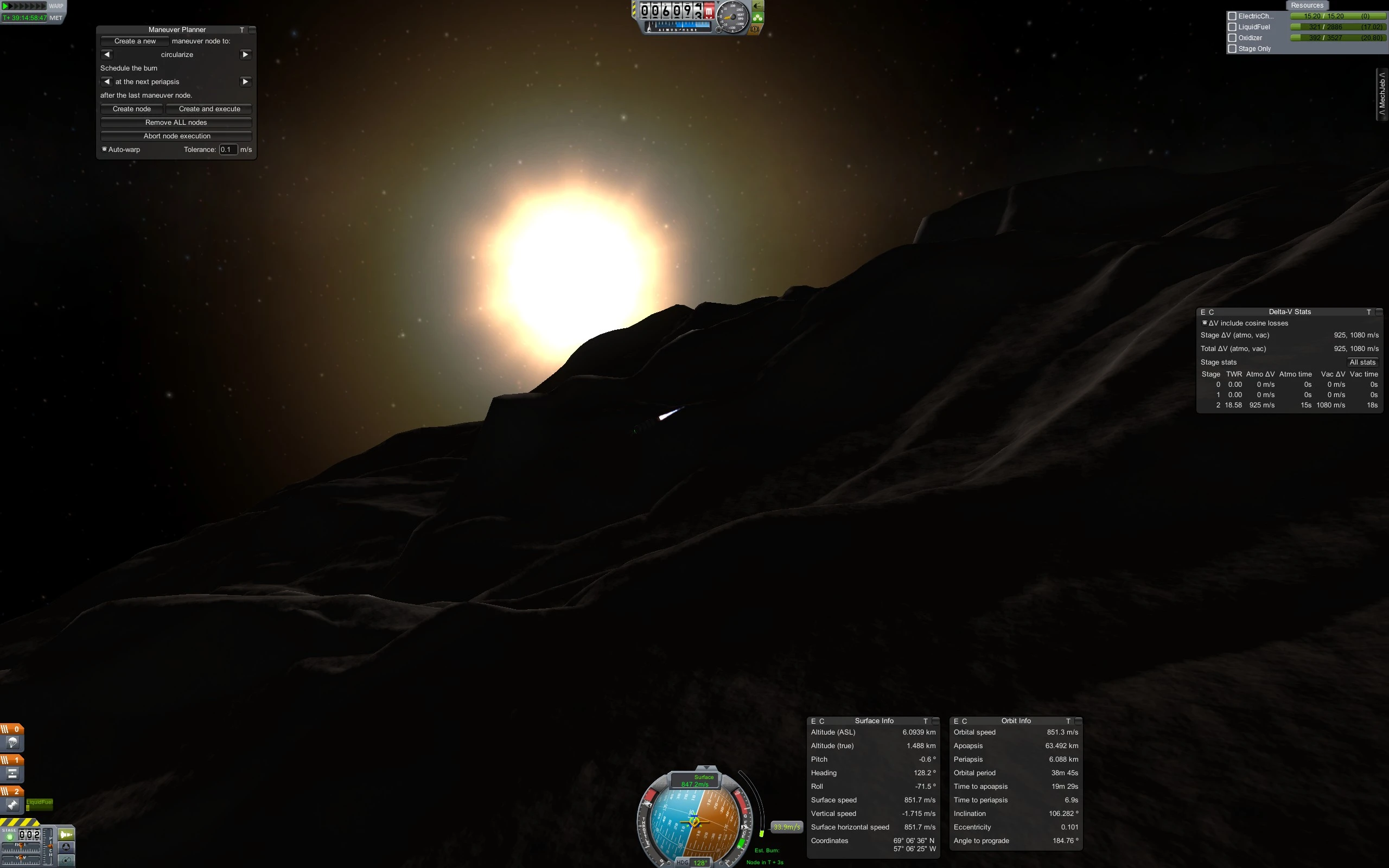
Kerbal Space Program is a game that, at its best, conveys the grandeur and majesty of space exploration. I suggest you put on an appropriate soundtrack and imagine the long, slow descent to the surface of the moon, in a craft surrounded by millions of miles of vacuum. Having traveled for days, shedding propellant and stages along your journey, until finally, your final stage hovers, whispering to a halt on jets of burning breath from your ancestral homeland–
one wheel touches–
Somewhere around January of 2014, I discovered Kerbal Space Program.
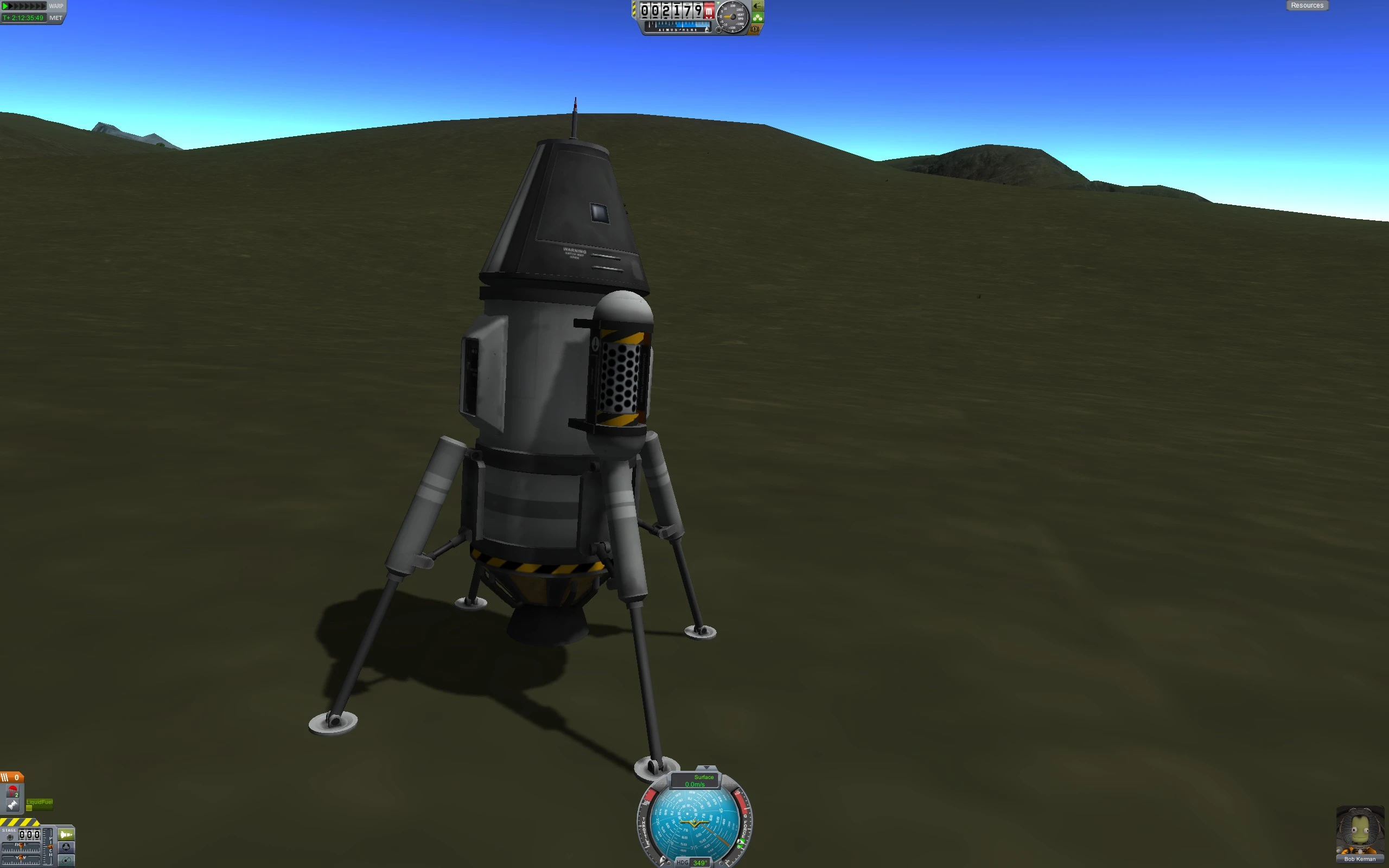
This was my first successful craft, which lifted off, flew a short distance from the pad, then (after several botched attempts and the deaths of several Kerbal pilots) touched down.
Prey is an perfectly serviceable AAA-class, science-fiction survival thriller game. It’s a first-person shooter, a stealth adventure, and a surprisingly enjoyable platformer. The plot is all right. The art is iconoclastic and gorgeous. As is traditional for the genre, much of the storytelling transpires through the environment: emails, voice logs, and diorama. There are some lovely ethical questions, both abstract and reified. For some reason, these are the things that people talk about when they talk about Prey.
After all, Prey is a videogame, and gameplay, art direction, and story are how we read videogames as texts. But I’d like to step back for a moment and talk about Prey’s symbolic and thematic choices, which are absolutely fucking fascinating. Spoilers ahead.
Penetration and Containment
Previously: Hexing the technical interview.
In the formless days, long before the rise of the Church, all spells were woven of pure causality, all actions were permitted, and death was common. Many witches were disfigured by their magicks, found crumpled at the center of a circle of twisted, glass-eaten trees, and stones which burned unceasing in the pooling water; some disappeared entirely, or wandered along the ridgetops: feet never touching earth, breath never warming air.
As a child, you learned the story of Gullveig-then-Heiðr, reborn three times from the fires of her trial, who traveled the world performing seidr: the reading and re-weaving of the future. Her foretellings (and there were many) were famed—spoken of even by the völva-beyond-the-world—but it was her survival that changed history. Through the ecstatic trance of seidr, she foresaw her fate, and conquered death. Her spells would never crash, and she became a friend to outcast women: the predecessors of your kind. It is said that Odin himself learned immortality from her.
Previously: Reversing the technical interview.
Long ago, on Svalbard, when you were a young witch of forty-three, your mother took your unscarred wrists in her hands, and spoke:
Vidrun, born of the sea-wind through the spruce
Vidrun, green-tinged offshoot of my bough, joy and burden of my life
Vidrun, fierce and clever, may our clan’s wisdom be yours:Never read Hacker News
If you want to get a job as a software witch, you’re going to have to pass a whiteboard interview. We all do them, as engineers–often as a part of our morning ritual, along with arranging a beautiful grid of xterms across the astral plane, and compulsively running ls in every nearby directory–just in case things have shifted during the night–the incorporeal equivalent of rummaging through that drawer in the back of the kitchen where we stash odd flanges, screwdrivers, and the strangely specific plastic bits: the accessories, those long-estranged black sheep of the families of our household appliances, their original purpose now forgotten, perhaps never known, but which we are bound to care for nonetheless. I’d like to walk you through a common interview question: reversing a linked list.
First, we need a linked list. Clear your workspace of unwanted xterms, sprinkle salt into the protective form of two parentheses, and recurse. Summon a list from the void.
(defn cons [h t] #(if % h t))
Last fall, I worked with CockroachDB to review and extend their Jepsen test suite. We found new bugs leading to serializability violations, improved documentation, and demonstrated documented behavior around nonlinearizable multi-key transactions. You can read the full analysis on jepsen.io.